RiceTeaCatPanda CTF - No Sleep
Hint gives us the website: https://riceteacatpanda.wtf/onlyrealgamers
There we have the following timer:
Looking at the page source code we have an interesting script:
<script src="https://cdnjs.cloudflare.com/ajax/libs/crypto-js/3.1.2/rollups/aes.js"></script>
<br><br><br><br><br><br><br><br><br><br>
Jess will let you be a real gamer in:
<p id="gamer timer"></p>
<script>
var _0x1d8e=['gamerfuel=Jan\x2027,\x202020\x2004:20:00','Jan\x2027,\x202020\x2004:20:00','getTime','exec','floor','getElementById','gamer\x20timer','AES','decrypt','U2FsdGVkX18kRm6FDkRVQfVuNPTxyOnJzpu8QnI/9UKoCXp6hQcley11nBnLIItj','ok\x20boomer','innerHTML','Utf8','cookie'];(function(_0x29eed8,_0x4bb4aa){var _0x47e29c=function(_0x2d3fd2){while(--_0x2d3fd2){_0x29eed8['push'](_0x29eed8['shift']());}};_0x47e29c(++_0x4bb4aa);}(_0x1d8e,0x99));var _0x2ad1=function(_0x545e19,_0x47cdd3){_0x545e19=_0x545e19-0x0;var _0x4275c2=_0x1d8e[_0x545e19];return _0x4275c2;};document[_0x2ad1('0x0')]=_0x2ad1('0x1');var countDownDate=new Date(_0x2ad1('0x2'))[_0x2ad1('0x3')]();var x=setInterval(function(){var _0x27a8c6=new Date(/[^=]*$/[_0x2ad1('0x4')](document[_0x2ad1('0x0')])[0x0])[_0x2ad1('0x3')]();var _0x5b92f1=new Date()['getTime']();var _0x3a5a33=_0x27a8c6-_0x5b92f1;var _0x4214a2=Math[_0x2ad1('0x5')](_0x3a5a33/(0x3e8*0x3c*0x3c*0x18));var _0x48c0d9=Math[_0x2ad1('0x5')](_0x3a5a33%(0x3e8*0x3c*0x3c*0x18)/(0x3e8*0x3c*0x3c));var _0x2de271=Math[_0x2ad1('0x5')](_0x3a5a33%(0x3e8*0x3c*0x3c)/(0x3e8*0x3c));var _0x240ffb=Math['floor'](_0x3a5a33%(0x3e8*0x3c)/0x3e8);document[_0x2ad1('0x6')](_0x2ad1('0x7'))['innerHTML']=_0x4214a2+'d\x20'+_0x48c0d9+'h\x20'+_0x2de271+'m\x20'+_0x240ffb+'s\x20';if(_0x3a5a33<0x0){clearInterval(x);var _0x1018af=CryptoJS[_0x2ad1('0x8')][_0x2ad1('0x9')](_0x2ad1('0xa'),_0x2ad1('0xb'));document[_0x2ad1('0x6')](_0x2ad1('0x7'))[_0x2ad1('0xc')]=_0x1018af['toString'](CryptoJS['enc'][_0x2ad1('0xd')]);}},0x3e8); __
</script>We see that it uses the AES module from the CryptoJS library.
Looking at the CryptoJS documentation we find the decryption function:
var decrypted = CryptoJS.AES.decrypt("Encrypted Message", "Secret Passphrase");And inside the script tags the only interesting part to us is:
'AES','decrypt','U2FsdGVkX18kRm6FDkRVQfVuNPTxyOnJzpu8QnI/9UKoCXp6hQcley11nBnLIItj','ok\x20boomer'Where the base64 looking string is the encrypted message and ‘ok boomer’ is the secret passphrase.
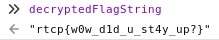
Running the commands below in the browser console we get the flag:
var decryptedFlag = CryptoJS.AES.decrypt("U2FsdGVkX18kRm6FDkRVQfVuNPTxyOnJzpu8QnI/9UKoCXp6hQcley11nBnLIItj", "ok boomer");
// Need to encode it to a string
var decryptedFlagString = decryptedFlag.toString(CryptoJS.enc.Utf8);